Data Protection for CareOn
Data Protection for CareOn
Table of Contents
Description
Web
Authentication
Curron Identifier
Data layer
General
Databases
Data protection
Description
The purpose of this document is to describe the data protection and security protocols pertaining the home care services within the CareOn system.
We will describe how web security is supported, user authentication and how data layers are set up to hide personal data.
Curron uses recognized security and data handling protocol. Curron relies on methods from Microsoft.
Web
The CareOn.is web uses HTTPS (HTTP over SSL). The RSA 2048-bit certificate ensures that server-user communication is encrypted.
All CareOn.is communications are through the web and encrypted with certificates.
The SSL certificate is certified by trusted parties and is therefore unique
Authentication
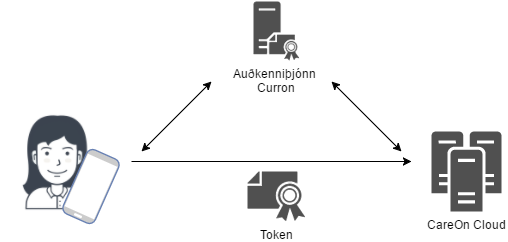
User authentication goes through Curron's authentication server. Authentication is "Federation Authentication", which ensures that no system components within CareOn can be accessed except by an authorized "Token" from Curron's authentication server.
This applies to sign-in from hands-free devices and via the web (CareOn.is)
CareOn users are the caretakers' team and team managers. Service receivers are generally not users.
Curron Identifier
The authentication server is accessible only through HTTPS and uses RSA 2048-bit SSL certificates from a trusted and accredited issuer.
Passwords are encrypted in a database and thus utilizes Microsoft Authentication.
Data layers
General
The CareOn home service databases are hosted by Origo, an ISO 27001 certified company and are closed behind a firewall. They are only accessible by (T3.Curron.is) home service systems and are not accessible from an outside network.
Microsoft SQL 2012 is used to host data.
Databases
Each data owner (municipality) has its own database (its own Scheme).
Database access is encrypted (Symmetric Key) with AES_256 algorithm. Encryption keys are marked with a certificate from the database.
Data protection
Relationships between individuals and services provided to individuals are encrypted on a database layer.
Encryption is achieved with Symmetric Key with AES_256 algorithm. Encryption keys are marked with a certificate from the database.
Connection between service receiver and the services provided is therefore encrypted on a database layer.